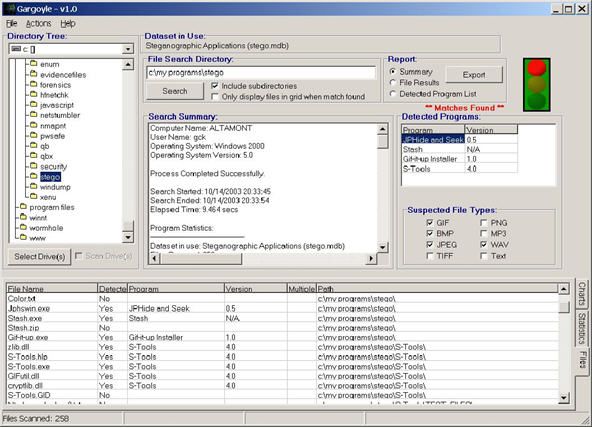
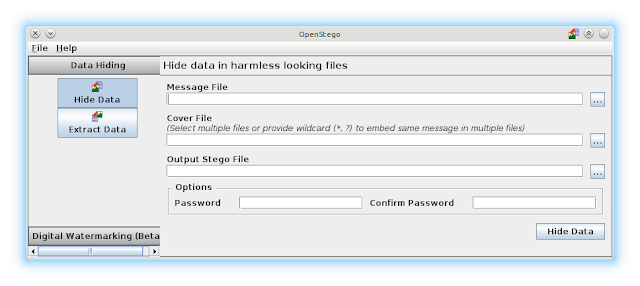
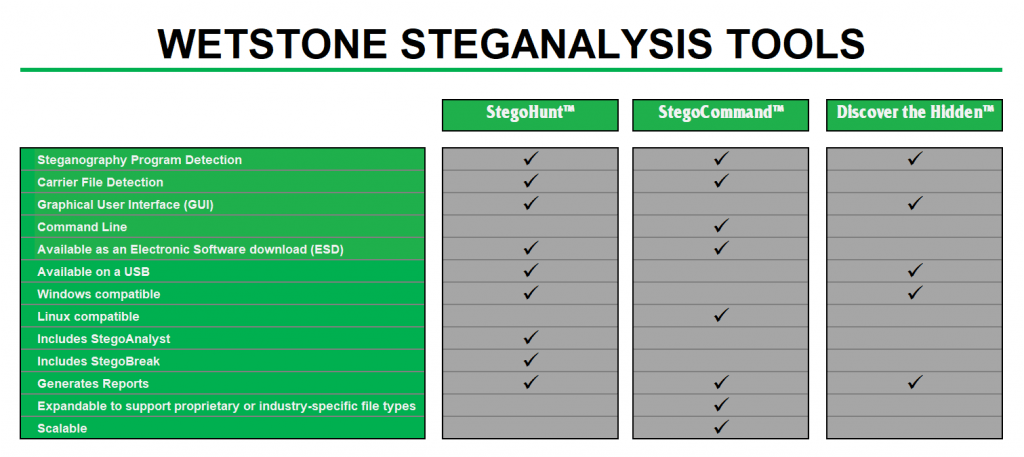
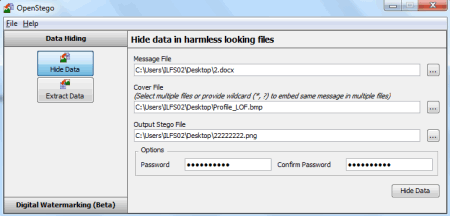
Use of steganographic tools like OpenStego, to detect data hiding or unauthorized file copying - YouTube

PDF) An Examination on Information Hiding Tools for Steganography | Resul DAŞ and Ismail KARADOGAN - Academia.edu

Business process flow and the interaction among data hiding tools and... | Download Scientific Diagram



![Data Hiding In Python: What is, Advantages & Disadvantages [With Coding Example] | upGrad blog Data Hiding In Python: What is, Advantages & Disadvantages [With Coding Example] | upGrad blog](https://www.upgrad.com/blog/wp-content/uploads/2021/02/1692.png)